基本原理 Linux在执行 动态链接的ELF时候,为了优化性能会使用一个 延迟绑定 的策略。
(延迟绑定:为了解决原本静态编译时要把各种系统API的具体实现代码都编译进ELF文件导致文件巨大臃肿的问题。)
当动态链接的ELF程序调用共享库的函数时,会去查找PLT表中的对应项目,PLT表在跳跃到GOT表中找到执行函数的实际地址,后续再调用的时候会直接去执行GOT表中对应的目标函数。(通过 _dl_runtime_solve()执行),
PLT Hook通过直接修改GOT表,使得在调用对应共享库的函数时跳转到用户自定义的Hook功能代码。
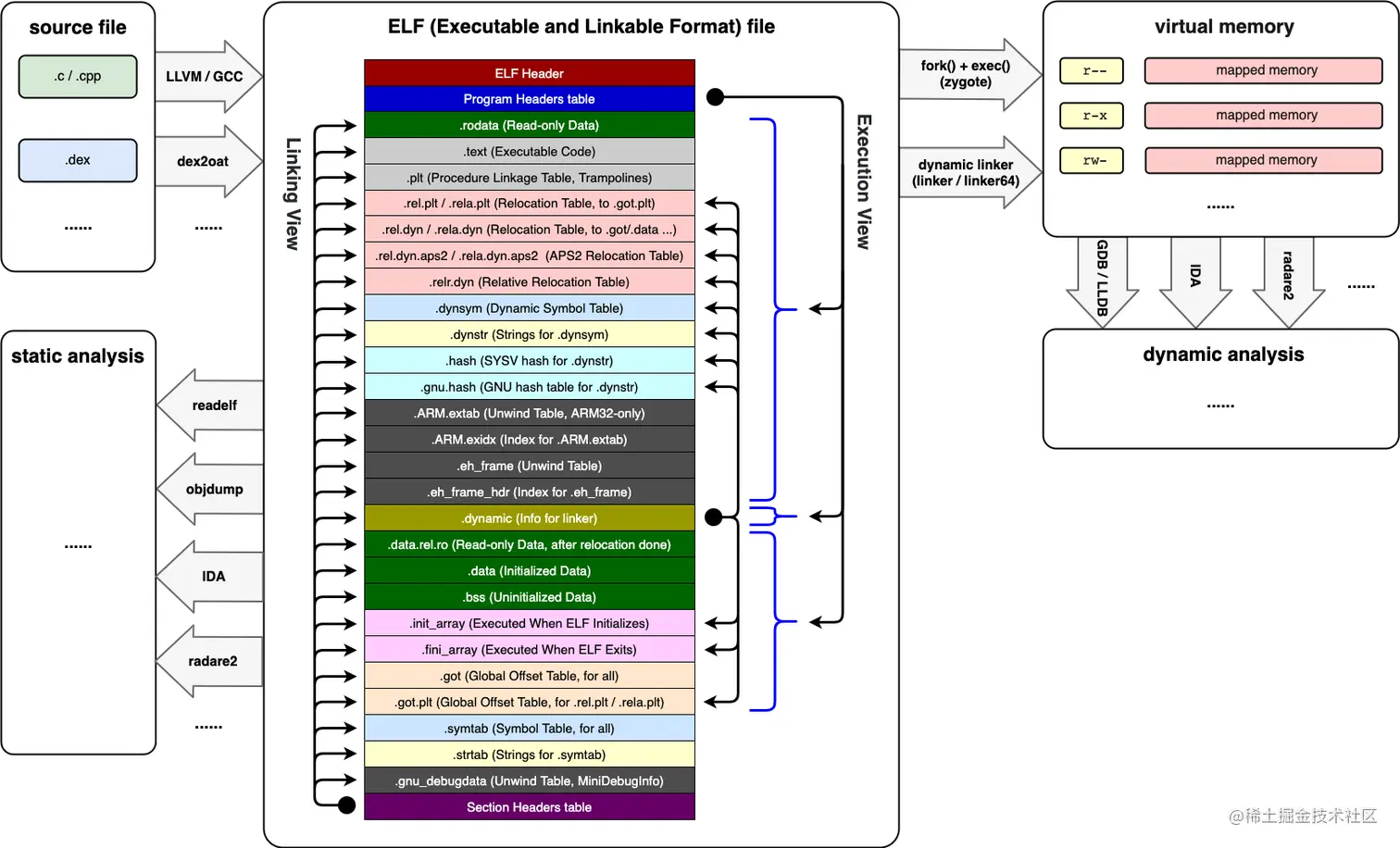
ELF
需要真正了解 PLT Hook的原理,需要从ELF开始,逐步的了解 linker(动态链接器)以及加载ELF文件的过程。
ELF格式
行业标准的二进制数据封装格式,主要用于封装可执行文件、动态库、object和coew dumps文件。
so库就是ELF格式的文件,了解了ELF结构是PLT Hook的基础知识。
用 readelf 可以查看ELF文件的基本信息。
用 objdump 可以查看ELF文件的反汇编输出。
ELF文件头
固定格式的定长文件头(32位架构为 52字节,64位架构为 64字节)。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 > aarch64-linux-android-readelf -h libbytehook.so
固定头字符 7f 45 4c 46 (后三个字符对应 E L F)
ELF被加载到内存时,以segment为单位,一个segment包含一个或多个section。
PHT则是用来记录所有 segment的基本信息。
主要包括如下信息:
segment类型
文件中的偏移量
大小
加载到内存后的虚拟内存相对地址
内存中字节对齐方式
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 aarch64-linux-android-readelf -l libbytehook.so
其中类型(Type)为 LOAD 的segment都会被 linker 通过mmap 映射到内存中。
ELF 以 section 为单位来组织和管理各种信息。使用 SHT 来记录所有section的基本信息。
主要包括:
section类型
文件中的偏移量
大小
加载内存后的虚拟内存相对地址
内存中的字节对齐方式
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 > aarch64-linux-android-readelf -S libbytehook.so
其中 starting at offset 0x4e0e8 对应 header中 Start of section headers: 319720 (bytes into file)
其中与 PLT Hook相关的Section如下:
.dynstr 保存所有字符串常量信息
.dynsym 保存符号(symbol)的信息。
符号的类型
符号起始地址
符号大小
符号名称在 .dynstr中的索引编号
.text 代码经过编译后生成的二进制机器指令
.data 已初始化的非只读数据
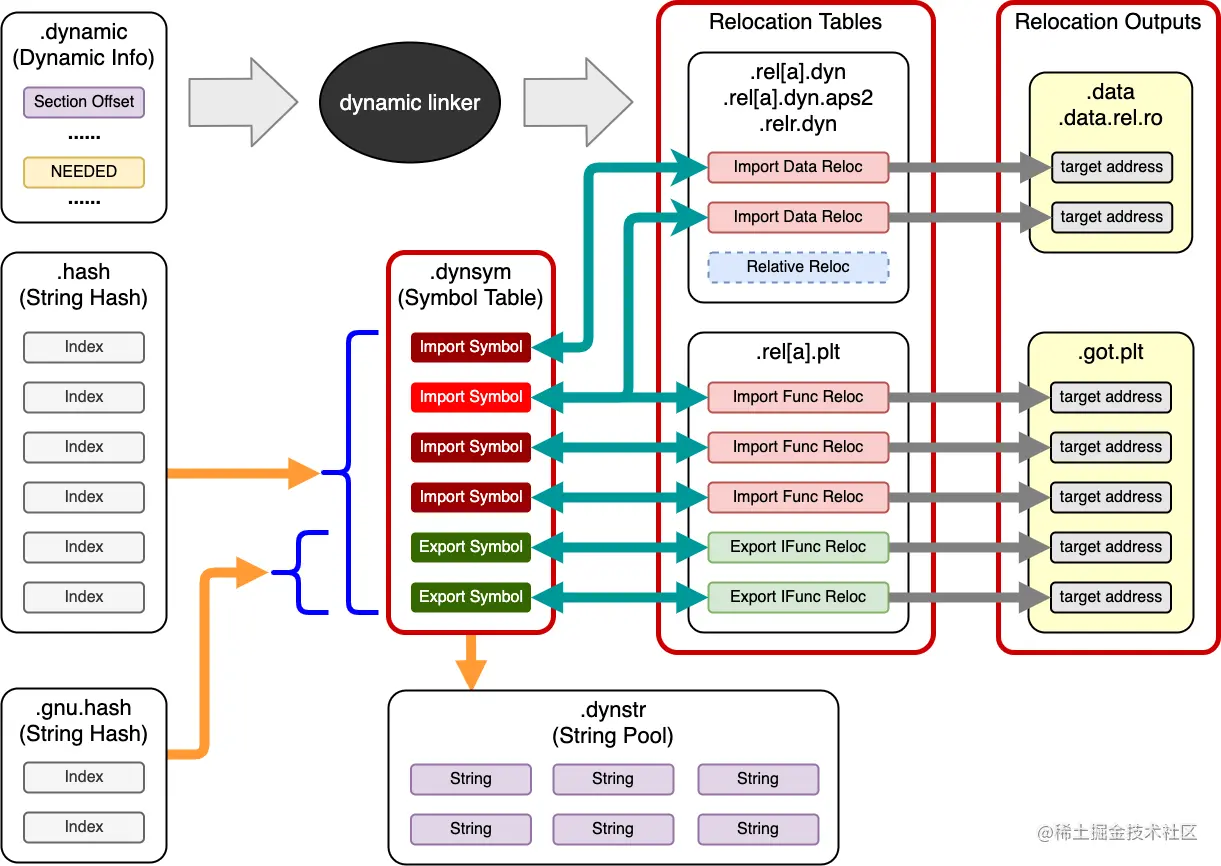
.dynamic 专门为linker设计的,记录了当前ELF的外部依赖,各个重要的section起始位置。
linker解析和加载ELF会用到的各项数据的索引信息。
.got.plt 给plt用的函数地址表,存储真实使用的函数地址
.got (Global Offset Table) 用于记录外部调用的入口地址,当linker执行 relocate 之后,表里会记录真实的外部调用绝对地址。
.plt (Procedure Linkage Table) 外部调用的跳板,主要用于支持 Lazy binding 方式的外部调用重定位。(目前只有MIPS架构支持)
.plt 会从 .got,.data,.data.rel.ro中查询符号的绝对地址,然后执行跳转。
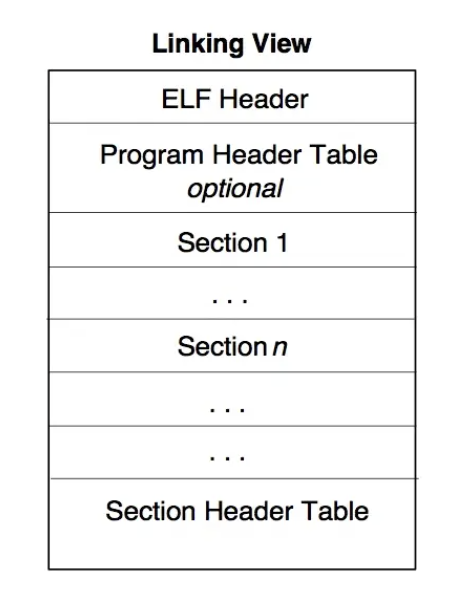
连接视图 - Linking View
ELF 未被加载到内存执行前,以section为单位的数据组织形式
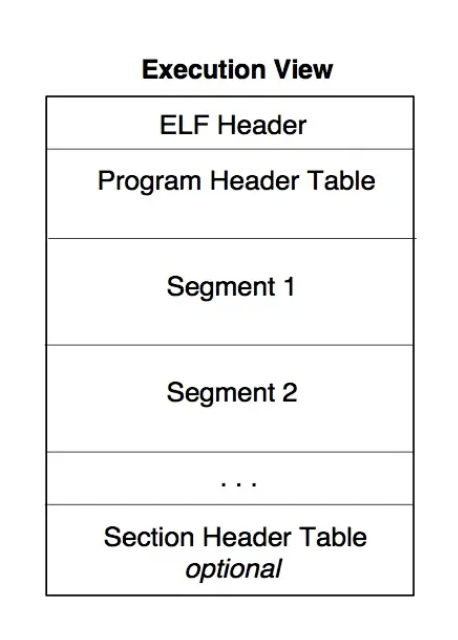
*执行视图 - Execution View
ELF 被加载到内存后,以 segment 为单位的数据组织形式
PLT Hook主要关心 执行视图 。
PLT Hook的执行时机是在 linker 使用 mmap 将ELF加载到内存中,再通过执行 relocation 把外部引用的绝对地址填入 GOT表和 DATA中。
* .dynamic section
专门为 linker 设计的,其中包含了 linker解析和加载ELF会用到的各项数据的索引信息。
对应 PHT中 type为 DYNAMIC的segment,再通过这个 segment 找到 .dynamic session。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 aarch64-linux-android-readelf -d libbytehook.so
参考文献 ELF概述
ELF完整结构
linker(动态链接器)
linker源码
大致步骤 动态链接(dlopen) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 void * do_dlopen (const char * name, int flags, const android_dlextinfo* extinfo, const void * caller_addr) find_library (ns, translated_name, flags, extinfo, caller);End ();if (si != nullptr ) {void * handle = si->to_handle ();LD_LOG (kLogDlopen,"... dlopen calling constructors: realpath=\"%s\", soname=\"%s\", handle=%p" ,get_realpath (), si->get_soname (), handle);call_constructors ();Disable ();LD_LOG (kLogDlopen,"... dlopen successful: realpath=\"%s\", soname=\"%s\", handle=%p" ,get_realpath (), si->get_soname (), handle);return handle;return nullptr ;
加载ELF 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 static soinfo* find_library (android_namespace_t * ns, const char * name, int rtld_flags, const android_dlextinfo* extinfo, soinfo* needed_by) nullptr ;if (name == nullptr ) {solist_get_somain ();else if (!find_libraries (ns,1 ,nullptr ,0 ,false )) {if (si != nullptr ) {soinfo_unload (si);return nullptr ;increment_ref_count ();return si;bool find_libraries (android_namespace_t * ns, soinfo* start_with, const char * const library_names[], size_t library_names_count, soinfo* soinfos[], std::vector<soinfo*>* ld_preloads, size_t ld_preloads_count, int rtld_flags, const android_dlextinfo* extinfo, bool add_as_children, std::vector<android_namespace_t *>* namespaces)
prelink_image
加载ELF中的 .dynamic section 从里面读取外部以来的ELF列表信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 bool soinfo::prelink_image (bool dlext_use_relro) if (flags_ & FLAG_PRELINKED) return true ;ElfW (Word) dynamic_flags = 0 ;phdr_table_get_dynamic_section (phdr, phnum, load_bias, &dynamic, &dynamic_flags);void phdr_table_get_dynamic_section (const ElfW(Phdr)* phdr_table, size_t phdr_count, ElfW(Addr) load_bias, ElfW(Dyn)** dynamic, ElfW(Word)* dynamic_flags) nullptr ;for (size_t i = 0 ; i<phdr_count; ++i) {const ElfW (Phdr) & phdr if (phdr.p_type == PT_DYNAMIC) {reinterpret_cast <ElfW (Dyn)*>(load_bias + phdr.p_vaddr);if (dynamic_flags) {return ;
link_image
执行 relocation 操作
1 2 3 4 5 6 7 8 9 10 11 12 13 14 bool soinfo::link_image (const SymbolLookupList& lookup_list, soinfo* local_group_root, const android_dlextinfo* extinfo, size_t * relro_fd_offset) if (this != solist_get_vdso () && !relocate (lookup_list)) {return false ;notify_gdb_of_load (this );set_image_linked ();return true ;
1 2 3 4 5 6 7 8 9 10 11 12 13 bool soinfo::relocate (const SymbolLookupList& lookup_list) if (relr_ != nullptr && !is_linker ()) {LD_DEBUG (reloc, "[ relocating %s relr ]" , get_realpath ());const ElfW (Relr) * begin const ElfW (Relr) * end if (!relocate_relr (begin, end, load_bias, should_tag_memtag_globals ())) {return false ;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 bool relocate_relr (const ElfW(Relr) * begin, const ElfW(Relr) * end, ElfW(Addr) load_bias, bool has_memtag_globals) constexpr size_t wordsize = sizeof (ElfW (Addr));ElfW (Addr) base = 0 ;for (const ElfW (Relr)* current = begin; current < end; ++current) {ElfW (Relr) entry = *current;ElfW (Addr) offset;if ((entry&1 ) == 0 ) {static_cast <ElfW (Addr)>(entry);apply_relr_reloc (offset, load_bias, has_memtag_globals);continue ;while (entry != 0 ) {1 ;if ((entry&1 ) != 0 ) {apply_relr_reloc (offset, load_bias, has_memtag_globals);8 *wordsize - 1 ) * wordsize;return true ;
执行重定位操作,这是最关键一步。
目的是为当前加载的ELF的每个导入符号找到对应的外部符号的绝对地址并写入到对应的位置里。
查询绝对地址
.rela.plt,.rel.plt:用于关联.got.plt和.dynsym,就是PLT表.rela.dyn,.rel.dyn:关联.data,.data.rel.ro,.dynsym
写入位置
.got.plt:保存外部函数的绝对地址,就是GOT表.data,.data.rel.ro:保存外部数据(函数指针)的绝对地址
.rela.*只在64位架构做了实现,相比.rel多了r_addend字段。
PLT:Procedure Linkage Table - 过程链接表
GOT:Global Offset Table - 全局偏移表
Hook原理 通过符号名,先在hash table中找到对应的符号信息(.dynsym)中,再从PLT表找到符号对应的信息,再从GOT表中找到绝对地址信息。通过修改GOT表中的绝对地址值,替换为Hook函数的地址。
作用边界(很重要) PLT Hook 本质上是修改导入方模块中的 GOT 表项,因此它的生效范围有明确边界:
能拦截:跨 so 的外部符号调用 (调用路径经过 PLT/GOT)。
通常不能拦截:同一 so 内部直接调用(不经过 PLT)、static 函数、被编译器内联/优化掉的调用。
需要注意:如果目标符号在链接期或运行期被特殊处理(如符号裁剪、-Bsymbolic、符号版本不匹配),可能无法命中 Hook。
一句话:PLT Hook 拦截的是“导入调用点”,不是“函数本体的所有执行路径”。
重定位类型:不只看 .rela.plt 很多资料只强调 .rela.plt,但工程里通常要同时关注多种重定位项:
JUMP_SLOT:典型的函数导入调用,对应 PLT/GOT 路径(最常见的 PLT Hook 目标)。GLOB_DAT:全局数据或函数地址类导入,常落在 .got/.data.rel.ro,有些 Hook 框架也会处理它。RELATIVE:用于基址修正,通常不是符号级 Hook 目标。
不同架构的重定位记录格式不同:
arm64 常见 RELA(带 addend 字段)。arm32 常见 REL(不带 addend 字段,附加值来自内存)。
因此在实现里建议按 DT_PLTREL / DT_RELA / DT_REL 分支解析,而不是写死只处理一种格式。
Hook时机与内存保护(NOW/LAZY + RELRO) PLT Hook 是否“马上生效”,与装载策略和内存保护强相关:
RTLD_NOW / BIND_NOW:加载期完成大部分符号解析,GOT 很早就被填好。RTLD_LAZY:首次调用时才解析 JUMP_SLOT,如果 Hook 安装太晚,可能错过第一次调用。RELRO(尤其 GNU_RELRO):重定位完成后,.got/.got.plt/.data.rel.ro 常被改为只读;写 GOT 前通常需要 mprotect 临时改写权限。
实践建议:
尽量在目标 so 完成加载且首次关键调用前安装 Hook。
写入前做页对齐并 mprotect(PROT_READ | PROT_WRITE),写入后恢复原权限。
记录 old/new 地址与返回码,失败时输出 errno 便于定位是时机问题还是权限问题。
常见失败场景(排查清单) PLT Hook 失败通常不是“代码没执行”,而是“调用路径不经过你改写的表项”:
-Bsymbolic:库内部对本库符号优先绑定,导致内部调用不走外部导入表。符号被优化:inline/static/LTO 等导致目标调用点被消除或改写。
符号版本不匹配:同名符号存在版本差异,按名称匹配可能命中错误项或无法命中。
linker namespace 隔离:目标库不在当前命名空间可见范围内,dlopen/dlsym 或遍历结果与预期不一致。
安装时机过晚:首次调用已发生,或已被其他框架先改写。
权限问题:RELRO 页未正确 mprotect,写入失败(通常伴随 errno)。
建议把“目标 so、符号名、重定位类型、旧地址/新地址、错误码”作为统一日志字段,优先确认“是否命中正确 GOT 表项”。
工程化最佳实践(稳定性) PLT Hook 建议至少补齐这些工程化能力:
幂等安装:同一 so + symbol 多次安装时要检测并避免重复写入。
线程安全:改写 GOT 时加锁,避免并发安装/卸载导致地址撕裂或状态错乱。
防递归调用:Hook 函数里调用链可能再次命中自身,需线程局部标记(TLS guard)防止无限递归。
可恢复(unhook):保存原始地址并支持回滚,便于灰度、故障止损和 A/B 对比。
白名单策略:只扫描和改写目标库/目标符号,避免全量遍历带来的性能与兼容性风险。
建议维护一张运行时状态表(目标库、符号、原地址、现地址、安装时间、状态码),用于排障与观测。
PLT Hook实践 以下是基于 三个自己编译的so进行的处理,代码逻辑相对简单。只为了熟悉基础的hook流程。如果需要更稳定的hook,还是推荐使用 相关三方库里的。
combined.cpp(待Hook类) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 #include <jni.h> #include <android/log.h> #define LOGI(...) __android_log_print(ANDROID_LOG_INFO, "PLT_COMBINED" , __VA_ARGS__) #define LOGE(...) __android_log_print(ANDROID_LOG_ERROR, "PLT_COMBINED" , __VA_ARGS__) extern "C" __attribute__((noinline)) int target_function (int x) LOGI ("target_function called with %d" , x);return x + 1 ;extern "C" JNIEXPORT jint JNICALL Java_com_example_plthookdemo_MainActivity_callTarget (JNIEnv* env, jobject thiz, jint v) LOGI ("callTarget: before calling target_function" );int r = target_function ((int )v); LOGI ("callTarget: after calling target_function, result=%d" , r);return r;
plthook.cpp(PLTHook类) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 #define _GNU_SOURCE #include <dlfcn.h> #include <link.h> #include <elf.h> #include <pthread.h> #include <unistd.h> #include <sys/mman.h> #include <android/log.h> #include <string.h> #include <errno.h> #include <stdint.h> #define LOGI(...) __android_log_print(ANDROID_LOG_INFO, "PLT_HOOK" , __VA_ARGS__) #define LOGE(...) __android_log_print(ANDROID_LOG_ERROR, "PLT_HOOK" , __VA_ARGS__) static const char COMBINED_SO[] = "libcombined.so" ;static const char TARGET_SYM[] = "target_function" ;typedef int (*target_fn_t ) (int ) static target_fn_t original_target_fn = nullptr ;extern "C" int hooked_target_function (int x) LOGI ("[HOOK] hooked_target_function called, arg=%d" , x);int new_arg = x + 200 ;int ret = 0 ;if (original_target_fn)original_target_fn (new_arg);else LOGE ("[HOOK] original_target_fn null!" );LOGI ("[HOOK] return %d" , ret);return ret;static bool make_writable (void * addr, size_t len) long page_size = sysconf (_SC_PAGESIZE); uintptr_t start = (uintptr_t )addr & ~(page_size - 1 );uintptr_t end = ((uintptr_t )addr + len + page_size - 1 ) & ~(page_size - 1 );size_t size = end - start;if (mprotect ((void *)start, size, PROT_READ | PROT_WRITE) != 0 ) {LOGE ("mprotect failed: %s addr=%p size=%zu" , strerror (errno), addr, size);return false ;LOGI ("mprotect success: addr=%p size=%zu" , addr, size);return true ;static bool process_relocations_64 (uintptr_t base, const Elf64_Phdr* phdr, int phnum) const Elf64_Dyn* dyn = nullptr ;for (int i = 0 ; i < phnum; i++) {if (phdr[i].p_type == PT_DYNAMIC)const Elf64_Dyn*)(base + phdr[i].p_vaddr);if (!dyn) return false ;const char * strtab = nullptr ; const Elf64_Sym* symtab = nullptr ; nullptr ; size_t rela_size = 0 ; for (const Elf64_Dyn* d = dyn; d->d_tag != DT_NULL; d++) {switch (d->d_tag) {case DT_STRTAB: strtab = (const char *)(base + d->d_un.d_ptr); break ;case DT_SYMTAB: symtab = (const Elf64_Sym*)(base + d->d_un.d_ptr); break ;case DT_JMPREL: rela = (Elf64_Rela*)(base + d->d_un.d_ptr); break ;case DT_PLTRELSZ: rela_size = d->d_un.d_val; break ;default : break ;if (!strtab || !symtab || !rela || !rela_size) {LOGE ("dyn info missing" );return false ;size_t n = rela_size / sizeof (Elf64_Rela);LOGI ("Scanning %zu PLT relocations" , n);for (size_t i = 0 ; i < n; i++) {size_t symidx = ELF64_R_SYM (r->r_info); const char * name = strtab + symtab[symidx].st_name; if (name && strcmp (name, TARGET_SYM) == 0 ) {uintptr_t got_addr = base + r->r_offset; LOGI ("Found symbol %s -> GOT %p" , name, (void *)got_addr);target_fn_t * got_entry = (target_fn_t *)got_addr;LOGI ("Original fn=%p" , (void *)original_target_fn);if (!make_writable (got_entry, sizeof (void *))) return false ;target_fn_t )&hooked_target_function;LOGI ("Patched GOT to %p" , (void *)hooked_target_function);return true ;return false ;static int phdr_cb (struct dl_phdr_info* info, size_t sz, void *) void )sz;if (!info->dlpi_name || !info->dlpi_name[0 ]) return 0 ;const char * name = strrchr (info->dlpi_name, '/' );if (name) name++; else name = info->dlpi_name;LOGI ("Inspected: %s" , name);if (strcmp (name, COMBINED_SO) == 0 ) {LOGI ("Matched combined: %s" , info->dlpi_name);process_relocations_64 (uintptr_t )info->dlpi_addr,reinterpret_cast <const Elf64_Phdr*>(info->dlpi_phdr),return 0 ; static void install_hook () LOGI ("Installing PLT hook..." );dl_iterate_phdr (phdr_cb, nullptr );LOGI ("PLT hook installed" );static void * delayed (void *) sleep (1 ); install_hook ();return nullptr ;static void onload () pthread_t t;pthread_create (&t, nullptr , delayed, nullptr );pthread_detach (t);LOGI ("plthook constructor executed" );
dl_iterate_phdr(遍历加载的so)
遍历当前进程中加载的所有ELF模块(.so / 主程序)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 struct dl_phdr_info {ElfW (Addr) dlpi_addr; const char *dlpi_name; const ElfW (Phdr) * dlpi_phdrElfW (Half) dlpi_phnum; int dl_iterate_phdr (int (*cb)(struct dl_phdr_info* info, size_t size, void * data), void * data) ElfW (Ehdr)* ehdr = reinterpret_cast <ElfW (Ehdr)*>(&__executable_start);if (memcmp (ehdr->e_ident, ELFMAG, SELFMAG) != 0 ) {return -1 ;struct dl_phdr_info exe_info;0 ;NULL ;reinterpret_cast <ElfW (Phdr)*>(reinterpret_cast <uintptr_t >(ehdr) + ehdr->e_phoff);0 ;0 ;const TlsModules& tls_modules = __libc_shared_globals()->tls_modules;if (tls_modules.module_count == 0 ) {0 ;nullptr ;else {const size_t kExeModuleId = 1 ;const StaticTlsLayout& layout = __libc_shared_globals()->static_tls_layout;const TlsModule& tls_module = tls_modules.module_table[__tls_module_id_to_idx(kExeModuleId)];char * static_tls = reinterpret_cast <char *>(__get_bionic_tcb()) - layout.offset_bionic_tcb ();int rc = cb (&exe_info, sizeof (exe_info), data);if (rc != 0 ) {return rc;ElfW (Ehdr)* ehdr_vdso = reinterpret_cast <ElfW (Ehdr)*>(getauxval (AT_SYSINFO_EHDR));if (ehdr_vdso == nullptr ) {return rc;struct dl_phdr_info vdso_info;0 ;NULL ;reinterpret_cast <ElfW (Phdr)*>(reinterpret_cast <char *>(ehdr_vdso) + ehdr_vdso->e_phoff);0 ;0 ;0 ;nullptr ;for (size_t i = 0 ; i < vdso_info.dlpi_phnum; ++i) {if (vdso_info.dlpi_phdr[i].p_type == PT_LOAD) {ElfW (Addr)) ehdr_vdso - vdso_info.dlpi_phdr[i].p_vaddr;break ;return cb (&vdso_info, sizeof (vdso_info), data);
CMakeLists.txt(SO编译配置) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 cmake_minimum_required (VERSION 3.10 )project ("plthook_combined" )set (CMAKE_CXX_STANDARD 17 )set (CMAKE_CXX_STANDARD_REQUIRED ON )add_library (combined SHARED combined.cpp)add_library (plthook SHARED plthook.cpp)target_link_libraries (combinedtarget_link_libraries (plthook
MainActivity(调用SO) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 package com.example.plthookdemoimport android.app.Activityimport android.os.Bundleimport android.util.Logimport androidx.appcompat.app.AppCompatActivityimport com.example.plthookdemo.databinding.ActivityMainBindingclass MainActivity : AppCompatActivity () {external fun callTarget (v: Int ) Int private lateinit var binding: ActivityMainBindingoverride fun onCreate (savedInstanceState: Bundle ?) super .onCreate(savedInstanceState)"PLT_TEST" , "Calling callTarget(5) ..." )val r = callTarget(5 )"PLT_TEST" , "callTarget returned: " + r)"123" val r = callTarget(5 )"PLT_TEST11" , "callTarget returned: " + r)companion object {init {"combined" );"plthook" );
总结 PLT Hook 的核心是:通过改写导入方的 GOT 表项,将外部符号调用重定向到自定义函数 。
在 Android 场景下,要把 PLT Hook 从“能跑”做到“可用”,关键在于三点:
理解边界 :只能稳定拦截经过导入表的调用;库内直调、inline/LTO、-Bsymbolic 等路径可能拦不到。 处理细节 :区分 REL/RELA 与重定位类型(如 JUMP_SLOT/GLOB_DAT),并正确解析 .dynamic 信息。 保证稳定性 :关注 RELRO/mprotect、安装时机(NOW/LAZY)、线程安全、幂等与可回滚能力。
相关要点
标准流程 :找目标 so -> 解析动态段 -> 匹配符号重定位项 -> 改 GOT -> 保存原函数并验证调用链。 高频追问 :为什么有些函数 hook 不到?(因为调用不经过导入表,或被优化/符号绑定策略改变) 架构差异 :arm64 常见 RELA,arm32 常见 REL。 与 Inline Hook 对比 :PLT Hook 侵入低、兼容性好但覆盖有限;Inline 覆盖广但复杂度和风险更高。 排障思路 :先确认是否命中目标 so/symbol,再看重定位类型、写入权限、old/new 地址与 errno。
一句话概括:PLT Hook 是“调用路径重定向”技术,价值在于低侵入拦截,难点在于边界识别与工程化稳定性。
相关三方库 bytedance/bhook
iqiyi/xhook
参考地址 字节跳动开源 Android PLT hook 方案 bhook